Видео с ютуба Phi(N) And D Using Rsa. Encrypt M=25

RSA Exampled MU Dec Solved | n=91 and public key e=5 find the value of p, q, phi(n) and d using RSA

RSA Exampled MU 24 Solved | n=221 and public key e=5 find the value of p, q, phi(n) and d using RSA

RSA Algorithm

How to Encrypt with RSA (but easy)

Calculation of "d" in RSA algorithm in English

RSA algorithm example|rsa algorithm encryption and decryption example|rsa example|rsa algorithm

The RSA Encryption Algorithm (1 of 2: Computing an Example)

9 RSA Encryption Algorithm

How the RSA algorithm works, including how to select d, e, n, p, q, and φ (phi)

Euler’s Totient Function (Phi Function)

How does Digital Signatures and Encryption actually work in the RSA Scheme - With Maths?

RSA Algorithm in Cryptography and Network Security

RSA algorithm | Decryption key | Cyber security | p=3 , q= 5, e=3 , m= 8

Attacking RSA by Factoring n Given phi(n)

Examples for RSA Cryptosystem

Public Keys Part 2 - RSA Encryption and Decryptions

RSA Risks: Selecting PHI which shares a factor with e

RSA Cryptography | Road to RSA Encryption #9
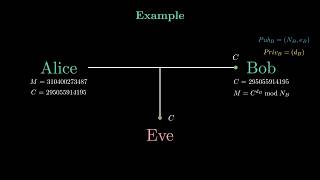
The RSA Encryption Algorithm - How Does It Actually Work + Step-by-Step Example.

Why RSA encryption actually works (no prior knowledge required)